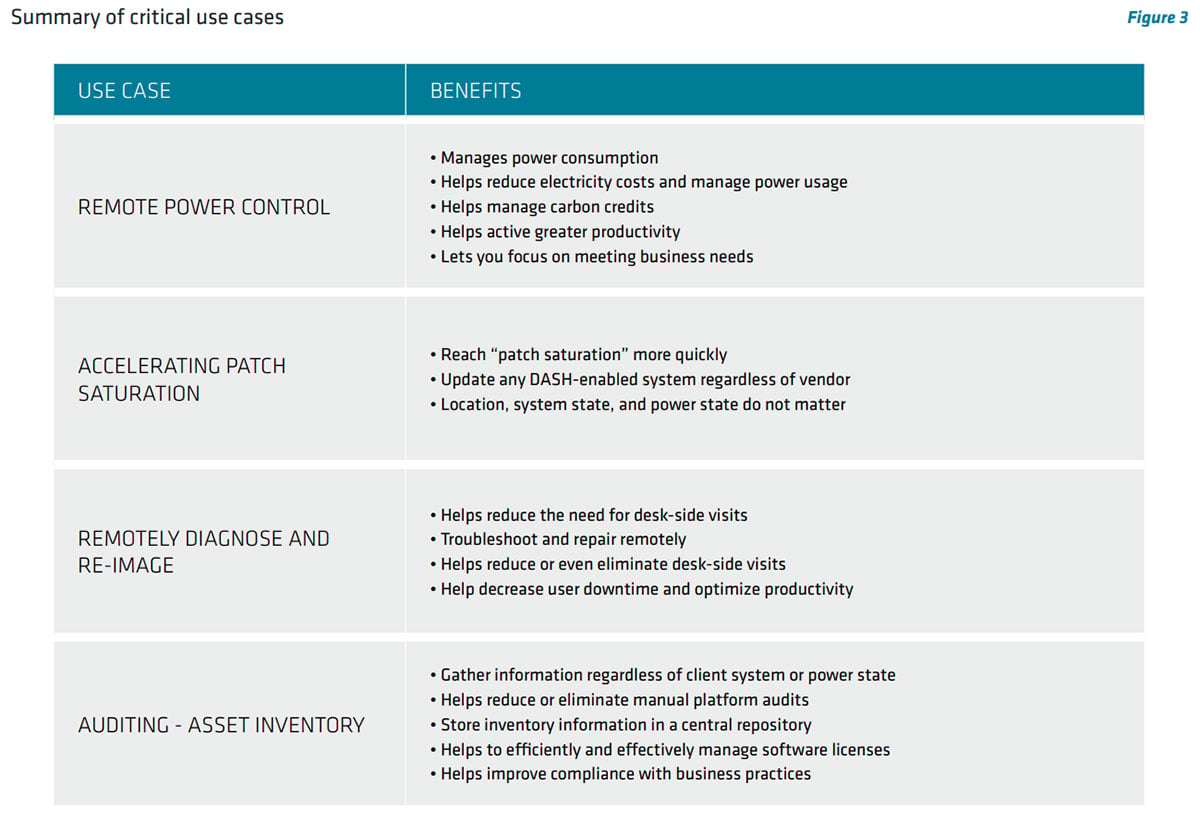
In Detail: AMD PRO Manageability Features
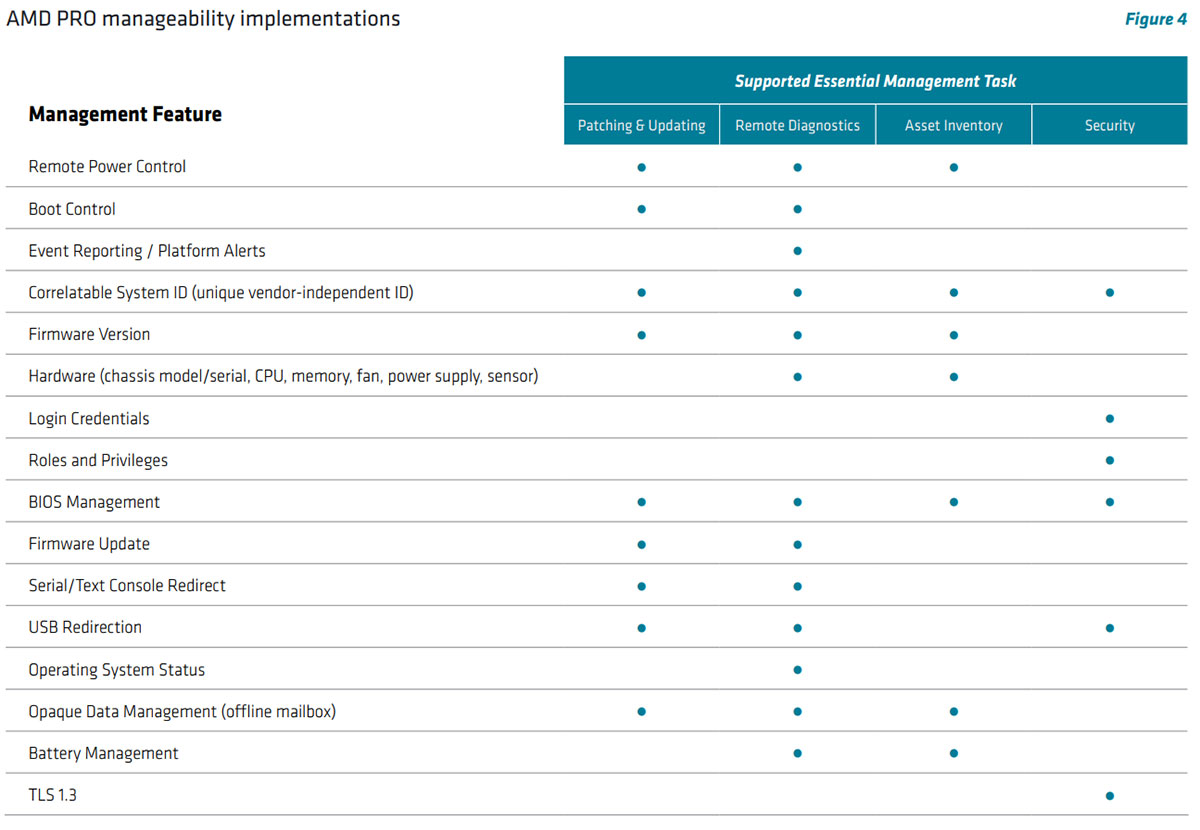
The management features defined by the DASH standard give IT administrators the ability to accomplish essential out-of-band client management tasks such as patching and updating, remote diagnostics, asset inventory, BIOS configuration, and security.
The following table (Figure 4) illustrates how DASH manageability features support these essential IT tasks. When implemented in DASH-enabled tools and technologies, these features will provide additional capabilities that further simplify client system management.
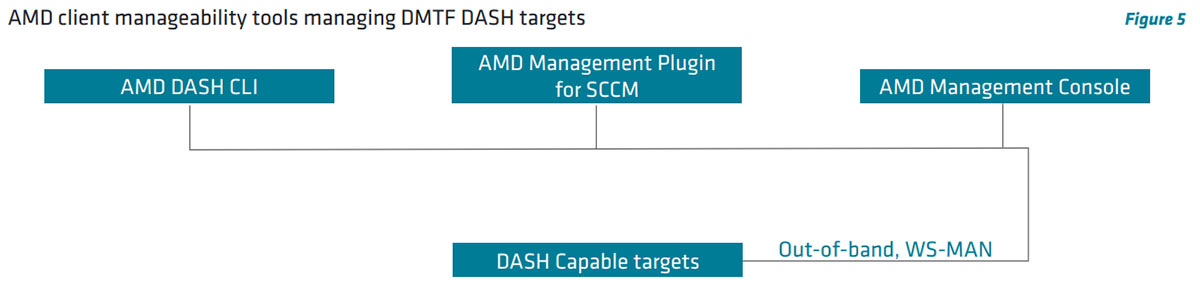
AMD PRO manageability provides multiple tools that can be used to manage supported systems via DASH standard for secure Out-ofBand (OOB) and Web Services Management (WS-MAN). Some of these solutions are standalone while others allow integration into existing in-band management solutions.
- AMD Management Plugin for SCCM (AMPS) – AMPS extends Microsoft System Center Configuration Manager (SCCM) and Microsoft Endpoint Configuration Manager (MECM) to support management tasks using DASH.
- AMD Management Console (AMC) – AMC is a GUI-based application for small business environments, capable of monitoring and managing up to 500 DMTF’s DASH-compliant clients. AMC supports KVM redirection for graphics-based BIOS setup screen.
- AMD DASH Command Line Interface (CLI) – AMD DASH CLI is an application used to perform out-of-band management tasks (power management, asset inventory, alerts, etc.) using DMTF DASH specifications (supports 2.33 DMTF schema) against a DASH target from a shell. AMD DASH CLI provides scripting interface and runs as a shell.
Dash Security
Securely managing clients is a fundamental part of daily client management. AMD PRO manageability supports security by providing DASH transport-level security and user-level security with supporting role-based authentication and authorization. These two levels of security give IT administrators the flexibility they need to control access to network resources and protect sensitive management data.
Transport-Level Security
DASH’s transport-level security ensures the integrity of messages sent between clients and management consoles, as well as authenticating the originating machine’s identity. It also offers encryption support for messages at the transport level. Because DASH specifies industry-standard protocols such as HTTPS and TLS for transport level security, IT administrators do not have to deal with complications arising from ports or worry about how management traffic is routed.
DASH delineates two classes of security:
Class A
Class A requires HTTP digest authentication, and no encryption capabilities are required beyond password encryption during digest authentication exchange. If implemented, MD5 digest algorithm is supported.
Class B
Class B defines three security profiles that are based on either TLS or IPsec with selected modes and cryptographic algorithms or cipher suites. For class B compliance, support for at least one of these security profiles is mandatory: TLS 1, TLS 2, IPsec.
The DASH implementation needs only to support either Class A or Class B, but for highest security the DASH implementation should be Class B compliant.
User-level Security
In addition to the transport-level security, DASH also defines role- based user-level security for authentication and authorization. The standard includes three operational roles that support user-level authentication and authorization:
- Read-only user: Allows the user to perform query and read operations on managed clients
- Operator: Allows the user to perform read, write, and execute operations on managed clients. Operators can change values, settings, and the state of managed clients.
- Administrator: Allows the user to perform read, write, execute, create, and delete operations on managed clients. Administrators can change values, settings, and the state of managed clients. They can also carry out user account management operations.
All DASH implementations must support the administrator role. The administrator performs account management for all other users.
In addition, the specification allows developers to add account management features to each role, as well as create additional roles as needed for finer control of access to various manageability functionality. By including role-based security, DASH-enabled solutions offer IT administrators considerable flexibility in assigning management tasks to different IT employees, purposely limiting the functionality to only those that need the functionality access.
Since DASH supports username/password and role-based authentication, DASH-enabled consoles and clients can be configured to use single sign-on authentication against a directory. DASH authentication can be transparently mapped to a Microsoft Active Directory.
When a user signs on to a DASH-enabled management console, the console looks up the credentials for the DASH SMSUSER in the directory and authenticates with the MAP on a managed resource using this login. While the MAP in this example would have to be separately configured with the credentials, the end result is single sign-on authentication and authorization for administrators.


